
The rapid digital transformation and widespread adoption of remote work have rendered traditional security perimeters less effective. As a result, identity has emerged as the new perimeter in the ever-evolving world of cybersecurity. By implementing Identity Threat Detection and Response (ITDR) strategies and integrating them with Extended Detection and Response (XDR) and Zero Trust frameworks, organizations can fortify their defenses against sophisticated cyber threats. In this article, we'll explore the role of ITDR, its relationship with XDR and Zero Trust, and the significance of quantifying risk for every identity based on real-time risk calculations.
Identity Compromise: The Startling Statistics
The importance of securing user identities cannot be overstated, as recent statistics reveal the magnitude of identity compromise:
82% of data breaches in 2022 were due to identity compromise, emphasizing the critical role of identity in cybersecurity (source: Verizon Data Breach Investigations Report, 2022).
Breaches caused by stolen or compromised credentials had the longest lifecycle — 243 days to identify the breach, and another 84 days to contain the breach. (source: Ponemon Institute, 2022).
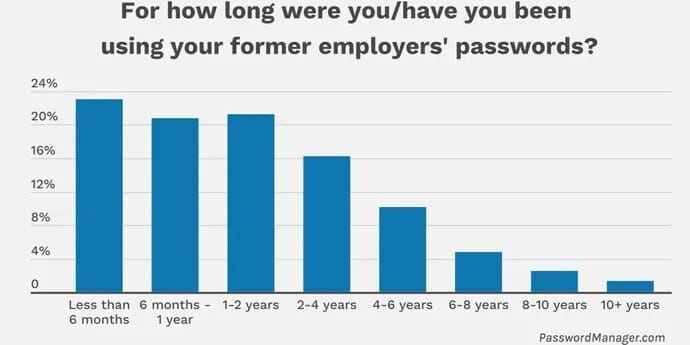
58% of former employees indicated they were still able to use their former company's passwords after they left. One in three respondents said they had been using the passwords for upwards of two years, which is a distressingly long time for organizations not to be aware of who is accessing those accounts and services. (source: PasswordManager.com, 2023)
Understanding the challenge
The Nature of Identity and Access
Dynamic and ever-changing: User identities and access privileges are constantly evolving as employees join, leave, or change roles within an organization. This fluidity makes it difficult to maintain an up-to-date baseline of legitimate access patterns, complicating the process of detecting unauthorized access.
Insider threats: Breaches involving compromised identity often stem from insider threats, which can be particularly challenging to detect. Insiders, such as employees or contractors, have legitimate access to sensitive information, making it difficult to discern between authorized and unauthorized activities.
The human element: The human factor plays a significant role in identity-related breaches, as users are often the weakest link in an organization's security chain. Phishing attacks, social engineering, and poor password hygiene can all lead to compromised credentials, further complicating the detection process.
Evolving Cyber Threat Landscape
Advanced attack techniques: Cybercriminals are increasingly deploying sophisticated attack methods, such as credential stuffing, password spraying, and multi-stage attacks. These techniques often involve multiple stages and can fly under the radar of traditional security measures, making it harder to detect identity compromise.
Lateral movement: Once an attacker gains access to a user's identity, they can leverage that access to move laterally within the organization, escalating privileges and gaining access to more sensitive information. This lateral movement can be difficult to detect, as it often mimics legitimate user behavior.
Limitations of Traditional Security Measures
Reactive approach: Traditional security measures, such as firewalls and antivirus software, are designed to respond to known threats. However, they often fail to detect identity-based attacks, which are inherently more subtle and can bypass perimeter defenses.
Lack of visibility: Many organizations lack complete visibility into their IT infrastructure, including user behavior, access patterns, and privileged account activities. This limited visibility hinders the ability to effectively detect and respond to identity-related breaches.
Access-as-a-Service: A new business model for cybercriminals
There is a new thriving business model in underground forums where so-called access brokers sell breached credentials or direct access to corporations everywhere to other criminals. Ransomware attackers, for instance, might not need to exploit a vulnerability or spam infectious emails to gain initial access — now they can just buy their way in.
Access brokers now offer what we call access as a service. These criminals provide other malicious actors a way into corporate networks for a price, paving the way for the actual damaging attacks. The existence of this new underground marketplace is the source of the disconnect between an initial corporate breach and the subsequent attacks that follow days or even months after.
Access brokers in the criminal underground often advertise this service like it’s a cinema ticket: Somebody buys this ticket, and they get straight in. In reality, however, things are a bit different. For example, what exactly do customers get in exchange for their money? Sometimes, it’s access to a web shell or a similar straightforward method of getting a command prompt into the compromised network. More often than not, however, it’s just a set of credentials and a virtual private network (VPN) server to connect to.
This also allows the seller to establish trust with the buyer from the very beginning, since it’s just a matter of logging into the network on a shared remote session and showing proof of having access to network resources. This would be the equivalent of walking with the customer into the compromised premises and showing them the interiors as proof that the stolen keys are real, like a twisted digital version of a real estate broker.
Most of the time, it is access brokers who bear the burden of the network breach that allows a ransomware attack to succeed. Even though ransomware still has by far the most visible impact during such a breach, the enablers of those attacks are usually the ones that quietly break and then sell access to other malicious actors.
Usually, profits from ransom payments tend to be divided into 80% for the ransomware group and 20% for whoever provided them the way in. We estimate that most of the time, ransomware attacks succeed because someone provided the ransomware group access to the target network, whether this someone is an access seller or a single hacker, as in the case study we previously discussed.
On a side note, in the affiliate model, the splits are reversed: The ransomware group receives 20%, and the affiliate receives 80%. In this model, the affiliates are expected to do the ransom negotiation; therefore, the payout is higher for them. Obviously, ransomware groups prefer the current access model that is becoming prevalent in the cybercriminal underground.
Because the ransomware payload is the most visible part of the attack, defenders tend to focus primarily on this. Consequently, most security discussions focus on ransomware attacks instead of on monitoring and mitigating the actions of access brokers. The same can be said regarding the media attention that ransomware groups regularly garner in contrast to access brokers.

ITDR: The New Line of Defense
Identity Threat Detection and Response (ITDR) solutions focus on identifying, detecting, and responding to threats targeting user identities and access privileges. By continuously monitoring user behavior and access patterns, ITDR systems can detect anomalies and flag suspicious activities that could indicate a compromised identity. Detecting a breach where identity has been compromised is particularly challenging for various reasons, including the dynamic nature of identity, the evolving cyber threat landscape, and the inherent limitations of traditional security measures.
The ITDR-XDR Connection
Extended Detection and Response (XDR) is an integrated, cross-platform approach to threat detection and response that consolidates data from multiple sources, including endpoints, email telemetry, network traffic, and cloud environments. Incorporating ITDR into an XDR strategy enables organizations to achieve a comprehensive view of their security landscape and effectively identify and remediate potential threats targeting user identities.
The Zero Trust Link
Zero Trust is a security framework centered on the principle of verifying every access request, regardless of user location or device used. Integrating ITDR with a Zero Trust architecture allows organizations to maintain a dynamic and continuous assessment of user identities, ensuring access is granted only to authenticated and authorized users.
Identity: a new component in Attack Surface
As the number of connected devices, applications, and services grows, so too does the attack surface – the aggregate of all potential vulnerabilities and entry points that could be exploited by cybercriminals. User identities are a crucial component of an organization's attack surface. Implementing ITDR reduces the attack surface by continually monitoring and analyzing user behavior, flagging potential threats, and minimizing unauthorized access.
Quantifying Risk for Every Identity
Effective cybersecurity strategies require organizations to assess and quantify risk for each user identity. By calculating real-time identity risk scores based on factors such as user behavior, access patterns, and device context, organizations can develop adaptive and dynamic responses to potential threats. ITDR solutions help achieve this by generating real-time risk assessments for each user, enabling organizations to tailor their response strategies accordingly.
Explaining the Importance of ITDR to a non-technical audience
Envision identity as a key to a house. If a burglar steals the key, they can easily access the house and its contents. ITDR acts like a vigilant security system that monitors who enters the house with the key, tracking their movements and raising an alarm if something appears suspicious.
Think of an airport's passport control. Travelers' identities are meticulously verified before they are allowed entry. ITDR serves as an advanced passport control system, scrutinizing user identities in real-time and flagging unauthorized or suspicious attempts to access sensitive information.
Final thoughts about the importance of ITDR and its integrations into a Cybersecurity Platform
As the cyber threat landscape evolves, the importance of identity in cyber security cannot be overstated. Identity Threat Detection and Response (ITDR) is critical for safeguarding user identities and ensuring the integrity of digital ecosystems. By quantifying risk for each user identity and calculating real-time identity risk scores and integrating ITDR with Extended Detection and Response (XDR) and Zero Trust frameworks, organizations can reduce cyber risk and enhance their cybersecurity posture, keeping their digital assets safe and secure in the face of increasingly sophisticated attacks.