
In the digital age, where the boundaries between the physical and virtual worlds are increasingly blurred, cybersecurity stands as one of the most critical concerns for organizations across the globe. The Cyber Risk Management Lifecycle is not merely a framework but a strategic compass guiding organizations through the complex terrain of digital threats. By adopting a risk-based cybersecurity strategy, businesses can allocate resources more efficiently, prioritize risks that could impact their most critical operations, and align their security initiatives with business objectives.
The imperative for a risk-based approach stems from the sheer volume and sophistication of cyber threats that modern enterprises face. A one-size-fits-all security strategy is no longer viable in a landscape where threat actors continuously evolve their tactics. Instead, organizations must adopt a more nuanced, strategic approach that emphasizes the management of risk over the impossible goal of eliminating all risk.
The Cyber Risk Management Lifecycle facilitates this by providing a structured methodology to identify, assess, mitigate, and monitor cyber risks in a continuous loop of improvement. It enables businesses to respond to the fluid nature of cyber threats with agility and informed decision-making. This approach ensures that cybersecurity efforts are not just reactive fire-fighting measures but are embedded in the fabric of organizational strategy, driving proactive defense mechanisms that protect critical assets while supporting business growth and innovation.
The Cyber Risk Management Lifecycle Framework
By leveraging the lifecycle of cyber risk management, organizations embolden their cybersecurity posture with a forward-thinking mindset. They can anticipate potential threats, understand their unique risk profile, and craft a cybersecurity strategy that is both resilient and adaptable. It's about creating a secure foundation upon which the future of the business can be built, in an environment where digital risks are acknowledged, understood, and managed with precision and foresight. Let's start exploring the first stage of this cycle:
Inventory, Contextualize & Value Digital Assets
The lifecycle commences with the identification and valuation of assets. In today's data-driven environment, assets extend beyond physical hardware to include any device, application connected to your digital infrastructure. Assigning value to these assets, based on their importance to the organization, is crucial for prioritizing risk management efforts.
Yet, amidst these varied assets, identities represent a particularly critical element. They are frequently targeted and exploited by cybercriminals in their attacks. Identities, whether they belong to employees, customers, or systems, encapsulate the access rights and privileges that enable the flow of information across the digital landscape. When these are compromised, the very integrity of an organization’s cybersecurity is put at risk. Therefore, the valuation process must give due consideration to identity assets, ensuring that their protection is central to the cybersecurity strategy. This initial phase of the Cyber Risk Management Lifecycle is where the foundation for a robust risk-based cybersecurity strategy is laid, setting the stage for the proactive measures that follow.
Identify Vulnerabilities, Threats & Consequences

Central to the Cyber Risk Management Lifecycle is the in-depth analysis of vulnerabilities, threats, and consequences, as illustrated by the intersecting circles of the diagram. Each component plays a critical role in the formulation of an organization's cybersecurity posture.
Vulnerabilities
These are the weaknesses within an organization's digital infrastructure that can be exploited by threats. They may exist due to outdated systems, unpatched software, misconfigurations, or even through more subtle means such as social engineering tactics. The red circle represents vulnerabilities, underscoring their potential to undermine the security framework.
Threats
Represented by the blue circle, threats are the actors or events with the potential to cause harm by taking advantage of vulnerabilities. These can range from external actors, like hackers and cybercriminal organizations, to internal threats, such as disgruntled employees or unintentional insider threats.
Consequences
The green circle signifies the potential consequences that can arise from threats exploiting vulnerabilities. These consequences can be far-reaching, impacting not only the organization’s operational capabilities but also its reputation, legal standing, and financial health.
Where these three elements intersect, we find cyber risk. The central area where the circles of threat, vulnerability, and consequence converge exemplifies the essence of cyber risk. It is the potential for loss or harm as a result of a threat actor exploiting a vulnerability, resulting in an undesirable consequence.
To manage this risk, an organization must have a thorough understanding of its vulnerabilities, the threats that could exploit them, and the potential consequences of such an event. This knowledge forms the basis for developing robust security measures and response plans.
For instance, a vulnerability in a piece of software could be exploited by a threat actor (threat) to gain unauthorized access to sensitive data, potentially leading to data theft, service disruption, or compliance violations (consequences). Understanding the interplay between these elements allows organizations to implement targeted measures to reduce their cyber risk profile, such as patch management, threat intelligence, and incident response planning.
By recognizing the interconnectedness of vulnerabilities, threats, and consequences, organizations can prioritize their cybersecurity efforts, focusing on the most significant risks that could impact their critical functions and strategic objectives. This approach not only enhances the organization's defensive capabilities but also ensures that cybersecurity investments are made strategically, with an eye towards minimizing potential impacts and maintaining operational resilience.
Cyber Risk Assessment, Profiling & Calculation
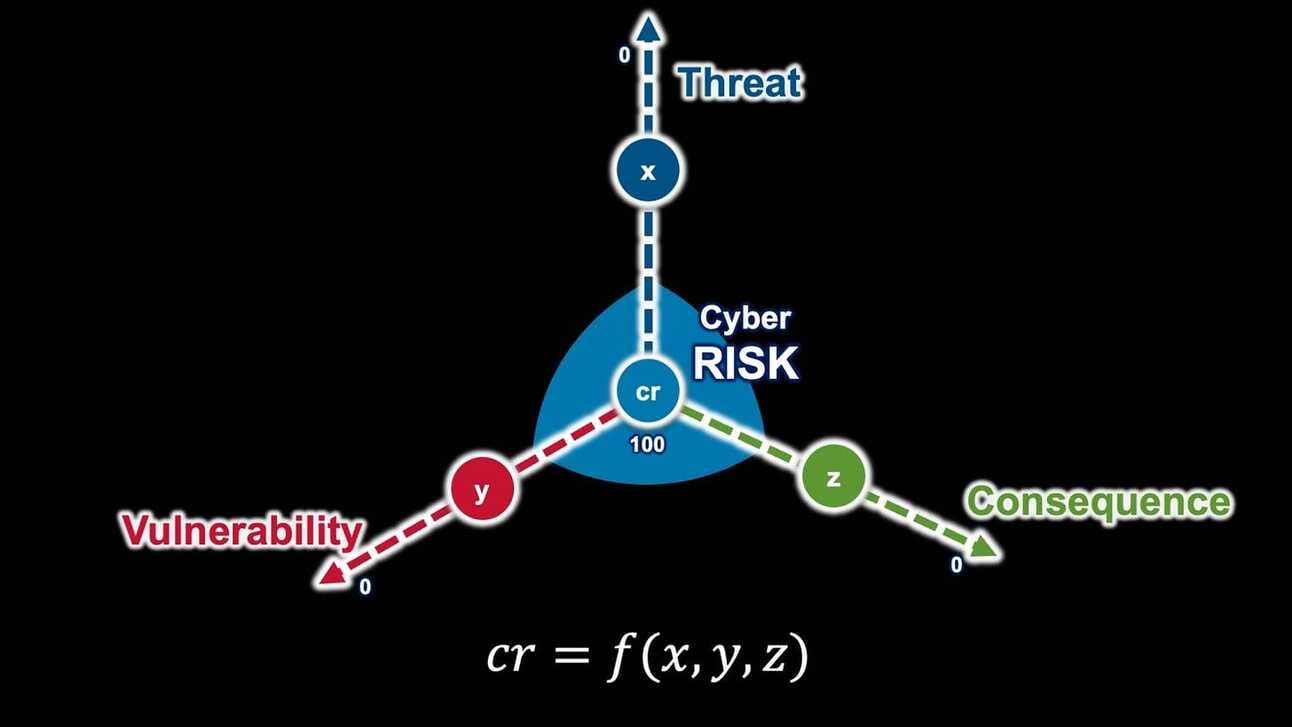
The Cyber Risk Assessment phase is a critical juncture in the Cyber Risk Management Lifecycle where quantitative and qualitative analysis methods converge. The conceptual model depicted in the diagram illustrates a mathematical approach to risk assessment, where cyber risk (cr) is evaluated as a function (f) of vulnerabilities (x), threats (y), and potential consequences (z).
Quantitative Assessment
In a quantitative assessment, each of these variables is assigned a numerical value, allowing for a more objective measure of risk. For instance, vulnerabilities could be scored based on severity, threats could be evaluated based on their likelihood, and consequences could be estimated in terms of potential financial loss or operational impact.
- The variable x quantifies the vulnerability, starting from 0 (no vulnerability) and scaling up based on the extent and severity of the weakness within the system.
- The variable y represents the threat level, which could be measured in frequency of attempts, sophistication of the threat actors, or the volume of threat incidents.
- The variable z captures the consequences, considering factors such as the sensitivity of the data at risk, the criticality of the affected systems, and the cost of potential downtime.
The 'cr' value at the center of the diagram represents the cyber risk score, which is calculated by combining these three variables. This score helps organizations prioritize their risks based on a clear metric, focusing their resources and efforts on areas with the highest score—signifying the greatest risk.
Qualitative Assessment
While the quantitative approach provides a numeric value to cyber risk, it is complemented by qualitative assessments, which provide context and insight into the nature of the risks. Qualitative analysis involves the expertise of cybersecurity professionals to interpret the data, assess the likelihood of risk scenarios, and understand the impact of risk in business terms.
Risk Profiling
The combination of quantitative and qualitative assessments leads to risk profiling. This involves categorizing risks into different levels or tiers based on their score and the business context. Each profile provides a snapshot of the risk's nature, including the potential attack vectors, affected assets, and recommended mitigation strategies.
Risk Calculation
The formula cr = f(x, y, z) is at the heart of risk calculation. It highlights the dynamic interplay between vulnerabilities, threats, and consequences. By adjusting the variables in this equation, organizations can simulate different scenarios and forecast the effectiveness of proposed security measures.
For instance, if a new security control reduces the vulnerability score (x), the overall cyber risk score (cr) should decrease, assuming other variables remain constant. This allows organizations to make data-driven decisions about their cybersecurity strategies.
The Cyber Risk Assessment, Profiling & Calculation phase is where organizations translate the complexities of cybersecurity into actionable intelligence. By quantifying and qualifying cyber risks, organizations can make informed decisions, allocate resources effectively, and build robust defenses that align with their overall risk tolerance and business strategy.
After finalizing the three initial phases of the Cyber Risk Management Lifecycle
Discover Assets & Asset Valuation
Identify Vulnerabilities, Threats & Consequences
Cyber Risk Assessment, Profiling & Calculation
We have finally mapped the digital terrain and attack surface of any modern organization, that is a complex three-dimensional landscape composed of devices, identities, applications, and the myriad of attack vectors that could potentially compromise them as you can read in this article Exploring the Attack Surface Landscape: A Comprehensive Cyber Risk Strategy

And now we can proceed to the next stages of the Cyber Risk Management Lifecycle Framework
Implement Defenses & Controls
Based on the risk assessment, the organization must implement appropriate defenses and controls. This may range from technical solutions, like firewalls and encryption, to administrative controls, like access policies and employee training programs.
Cyber Risk Mitigation
Mitigation strategies are developed to reduce the impact of cyber threats. This includes not only deploying technological solutions but also ensuring that processes are in place for swift response in the event of a security incident.
Cyber Risk Tracking & Monitoring
Ongoing monitoring and tracking are essential to manage cyber risk effectively. Continuous oversight ensures that the organization can detect and respond to threats in real-time, adapting their defense mechanisms as the threat landscape changes.
Cyber Risk Reassessment
In the dynamic arena of cyber threats and business operations, a static approach to risk management is a recipe for vulnerability. The velocity at which business processes evolve, alongside the rapidly changing landscape of cyber threats, necessitates a perpetual cycle of Cyber Risk Reassessment. This phase is not the conclusion of the lifecycle but an integral, ongoing process that feeds back into the lifecycle, ensuring that risk management strategies remain relevant and effective.

Adapting to the Speed of Business
Today’s business environment is characterized by swift changes – new products are launched, new markets are entered, and new technologies are adopted. Each of these developments can alter an organization's risk profile. What was secure yesterday may not be secure today. For instance, the integration of new software or the expansion into cloud services can open new avenues for cyber threats. Continuous reassessment allows organizations to recalibrate their cybersecurity posture in alignment with their current business model and objectives.
Keeping Pace with the Speed of Attacks
Cybercriminals are continually evolving their tactics. The tools and techniques that were considered advanced yesterday are today's standard practice among threat actors. Ransomware, phishing, and sophisticated state-sponsored attacks are becoming more frequent and more ingenious. Organizations must reassess risks to anticipate these threats and prevent breaches that could have dire consequences.
Continuous Reassessment Cycle
Cyber Risk Reassessment is a continuous cycle that includes:
Monitoring for new threats and vulnerabilities.
Reviewing the impact of organizational changes on security posture.
Assessing the effectiveness of current cybersecurity controls.
Identifying emerging trends in the threat landscape.
Adjusting risk mitigation strategies in response to feedback and analysis.
This process is not a one-off event but a disciplined, regular review that's as agile and proactive as the threats it aims to counteract. It’s about creating a feedback loop where lessons learned from monitoring and incidents are used to inform the reassessment process, leading to refined and updated security measures.
The Strategic Importance of Reassessment
The strategic importance of reassessment cannot be overstated. It supports informed decision-making and ensures that risk management remains a board-level concern, integrated with strategic business planning. Cybersecurity is not a cost center but a dynamic capability that protects and adds value to the business. As such, Cyber Risk Reassessment is a business enabler, allowing organizations to take calculated risks in pursuit of innovation and growth while maintaining a secure and resilient operational environment.
In conclusion, Cyber Risk Reassessment is the critical process that keeps the Cyber Risk Management Lifecycle active and effective. By continuously reassessing their cyber risk posture, organizations can ensure that they are not just responding to the current threat environment but are prepared for the future, safeguarding their assets, reputation, and strategic ambitions against the threats of tomorrow.
Final thoughts
The Cyber Risk Management Lifecycle is a comprehensive framework that underscores the dynamic nature of cybersecurity. Organizations that adopt this lifecycle approach will be better equipped to manage their cyber risks proactively and align their cybersecurity posture with strategic business outcomes. Leveraging this diagram as a guide, cybersecurity leaders can foster an organizational culture that values continuous improvement and resilience against the ever-present cyber threats.